Introduction: The New Face of State-Backed Cyberwarfare
In the ever-evolving landscape of cyber threats, 2025 has already proven to be a volatile year. This time, it’s the Russia-linked threat actor COLDRIVER—also known as Callisto, Star Blizzard, or UNC4057—resurfacing with a chilling new weapon in its digital arsenal: LOSTKEYS malware, distributed using an increasingly popular social engineering trick dubbed ClickFix.
While nation-state hacking is nothing new, the sophistication, scope, and psychological manipulation involved in this campaign reveal how threat actors are evolving faster than defenses. And more importantly, how their tactics are becoming eerily personal.
Who Is COLDRIVER?
COLDRIVER is not your run-of-the-mill hacker group. Linked to Russian intelligence, this actor has a notorious track record of espionage targeting Western military advisors, journalists, NGOs, and more recently, individuals with ties to Ukraine. Their methods often involve credential phishing, but LOSTKEYS marks a significant escalation—moving from passive surveillance to active endpoint compromise.
Their goal? Exfiltrate high-value data, hijack user environments, and quietly disappear—leaving almost no trace.
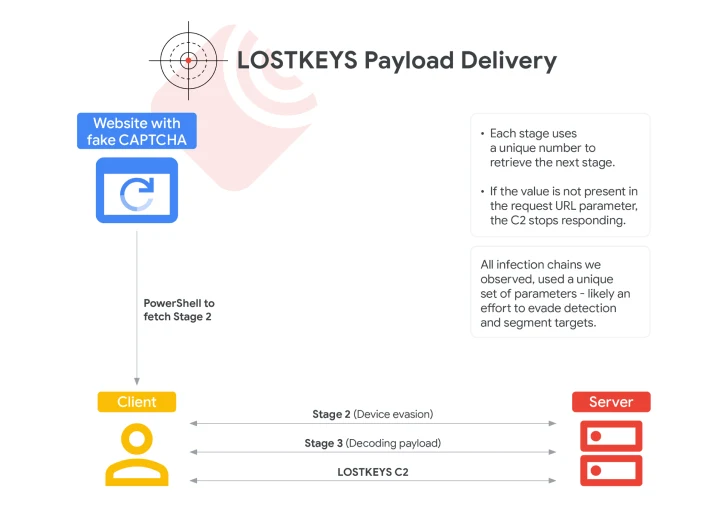
What Is LOSTKEYS?
LOSTKEYS is a new, custom-built malware observed in attacks spanning January to April 2025, designed to:
- Harvest files from a hard-coded list of extensions and directories
- Capture system metadata like running processes and hardware specs
- Transmit this data back to the attacker via covert channels
It’s surgically precise, deployed only in high-value targets, and serves as a surveillance tool capable of adapting to various environments. Think of it as a spy who sneaks into your digital home, rifles through your drawers, and quietly leaves before you know they were there.
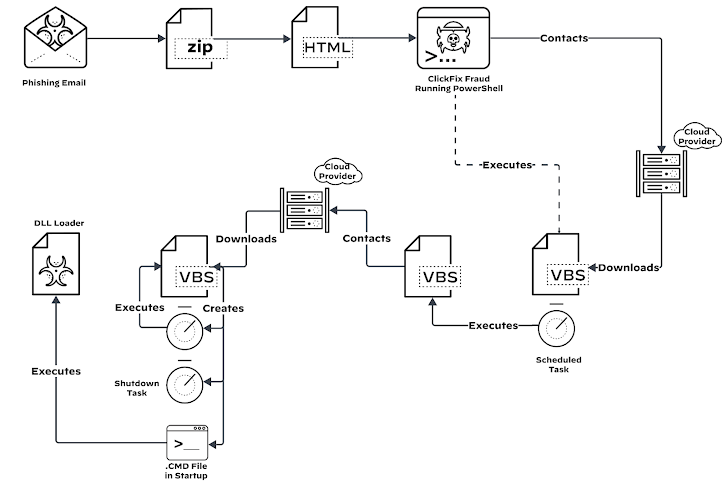
The Social Engineering Trap: ClickFix
The initial attack vector is a masterclass in psychological manipulation.
Victims land on a decoy website with a fake CAPTCHA, prompting them to “verify” they’re human. But instead of solving a puzzle, they’re instructed to:
- Open the Windows Run dialog
- Paste a pre-copied PowerShell command from the clipboard
- Execute the command manually
This method—known as ClickFix—sidesteps many traditional defenses. There’s no exploit. No file download. Just social engineering at its finest.
Once executed, the PowerShell script:
- Connects to a command server
- Downloads a third-stage payload
- Deploys LOSTKEYS after performing virtual machine checks (to avoid detection in research labs)
The Bigger Picture: From SPICA to LOSTKEYS
LOSTKEYS isn’t COLDRIVER’s first dance with malware. It follows SPICA, another custom tool that marked the group’s pivot from phishing to endpoint infiltration. What makes LOSTKEYS more concerning is its selective deployment. It’s not built for mass infection—it’s tailored for precision espionage.
Think of it as a digital sniper, not a bomber.
Collateral Campaigns: ClickFix Goes Global
COLDRIVER isn’t the only actor exploiting ClickFix. In parallel campaigns:
- Lampion banking trojan was delivered to Portuguese-speaking users via fake ZIP attachments.
- Atomic Stealer, a macOS-focused infostealer, leveraged a variant using Binance Smart Chain (BSC) contracts and EtherHiding tactics to embed payloads in blockchain transactions.
- Over 2,800 compromised websites have been weaponized to serve fake CAPTCHA prompts, part of a larger watering hole operation called MacReaper.
This underscores a grim reality: ClickFix is becoming a malware distribution standard, not an anomaly.
Human Impact: Not Just Numbers
This isn’t just about cybersecurity buzzwords. The victims here are journalists, civil society workers, and government advisors—individuals who may never realize they were compromised. Their personal emails, confidential documents, and even sources could have been siphoned off into state-controlled intelligence pipelines.
For them, the stakes are existential.
Imagine a Ukrainian war analyst who unknowingly executes a ClickFix command. That single click could compromise not just their files—but their entire network of contacts.
What Can You Do?
- Train Your Teams: Awareness is key. Employees and collaborators must be trained to spot unusual CAPTCHA behaviors or odd requests to run commands.
- Monitor for PowerShell Usage: Use endpoint detection tools that flag suspicious PowerShell execution, especially those copying from clipboards.
- Isolate High-Risk Browsing: Open untrusted links in virtual or sandboxed environments.
- Patch and Update: While ClickFix bypasses traditional exploits, newer systems offer better monitoring and execution policies.
- Avoid Copy-Paste from Unknown Sites: It seems simple, but it’s one of the most effective defenses.
Conclusion: A Warning Wrapped in a CAPTCHA
LOSTKEYS and ClickFix aren’t just technical threats—they’re a psychological warfare tool in digital disguise. They remind us that the human element remains the most vulnerable vector in cybersecurity.
Whether it’s COLDRIVER, Lampion, or Atomic Stealer, one thing is clear: cyber attackers are no longer hacking systems—they’re hacking people.
Stay vigilant. Stay informed. And above all, never trust a CAPTCHA that asks you to open Run.
Share your thoughts: Have you seen suspicious CAPTCHA behavior recently? Have you encountered unusual PowerShell prompts while browsing? Let us know in the comments or reach out to our threat research team.















Add comment