Introduction
In a bold counterattack, cybersecurity researchers from Resecurity managed to breach the infrastructure of the BlackLock ransomware gang, exposing their secret operations. By exploiting a Local File Inclusion (LFI) vulnerability in BlackLock’s Data Leak Site (DLS), the researchers obtained sensitive information, including server configurations, credentials, and command histories.
This unexpected infiltration offers a rare glimpse into the inner workings of one of the most aggressive ransomware groups in 2025. Here are five shocking revelations from this unprecedented hack.
1. Hackers Become the Hacked
In an ironic turn of events, Resecurity exploited a misconfiguration in BlackLock’s DLS, allowing them to:
- Access clearnet IP addresses behind the group’s TOR hidden services.
- Retrieve command execution logs, offering a detailed view of BlackLock’s internal operations.
- Extract authentication credentials and configuration files.
This represents one of the most significant OPSEC (Operational Security) failures by a ransomware group, leaving their infrastructure exposed.
2. BlackLock’s True Identity Revealed
The breach confirmed that BlackLock is actually a rebranded version of Eldorado ransomware, an earlier extortion group. Since its relaunch, BlackLock has become one of the most active ransomware gangs of 2025, targeting industries such as:
- Technology
- Finance
- Manufacturing
- Retail
- Construction
As of March 2025, BlackLock has claimed 46 victims across 15 countries, including:
- 🇺🇸 United States
- 🇫🇷 France
- 🇧🇷 Brazil
- 🇬🇧 United Kingdom
- 🇨🇦 Canada
- 🇦🇪 United Arab Emirates
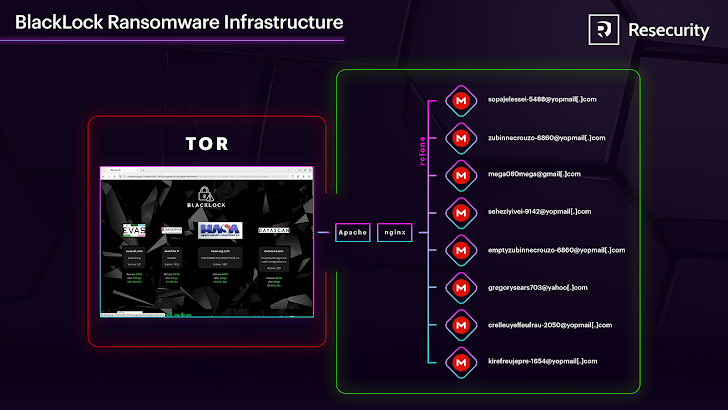
3. Cloud-Powered Data Theft
The infiltration revealed BlackLock’s data exfiltration techniques. The group uses Rclone, a popular command-line tool, to transfer stolen data to MEGA cloud storage. In some cases, they even install the MEGA client on victim systems to speed up the exfiltration process.
Resecurity uncovered at least eight MEGA accounts linked to BlackLock, all created using temporary YOPmail addresses (e.g., zubinnecrouzo-6860@yopmail.com) to conceal their identities.
4. DragonForce Connection: Shared Code and Rivalry
The analysis revealed striking similarities between BlackLock’s ransomware source code and the DragonForce ransomware strain that previously targeted organizations in Saudi Arabia. Key overlaps include:
- Encryption algorithms and ransom note formats.
- Command execution methods and internal coding patterns.
Interestingly, while DragonForce is written in Visual C++, BlackLock is coded in Go, indicating potential collaboration or code repurposing between the two groups.
5. Ransomware Rivalry: BlackLock Gets Defaced
In a dramatic twist, DragonForce retaliated by hacking and defacing BlackLock’s DLS on March 20, 2025. Researchers believe DragonForce exploited the same LFI vulnerability to breach BlackLock’s infrastructure.
Just a day earlier, Mamona ransomware—an affiliate project linked to BlackLock—also had its DLS defaced, suggesting internal conflicts or rivalries between competing ransomware factions.
✅ Key Takeaway: Hackers’ OPSEC Failure Exposes Their Secrets
The BlackLock breach reveals a surprising vulnerability in the operations of elite ransomware groups. It also underscores how security researchers can flip the script by exploiting weaknesses in the attackers’ own infrastructure.
This incident highlights the importance of:
- Strengthening cybersecurity defenses to prevent ransomware attacks.
- Employing advanced threat detection and incident response strategies.
- Remaining aware of evolving ransomware tactics to safeguard sensitive data.
By infiltrating BlackLock, Resecurity has not only exposed a major ransomware operation but also disrupted its extortion activities—proving that sometimes, even the hackers get hacked.















Add comment