Introduction
A notorious cybercrime group known as Golden Chickens, also tracked as Venom Spider, has recently resurfaced with two new malware strains—TerraStealerV2 and TerraLogger—as part of their evolving malware-as-a-service (MaaS) portfolio. According to a recent report from the Insikt Group at Recorded Future, these tools are specifically engineered to target browser credentials, cryptocurrency wallets, and user keystrokes, signaling the group’s continued commitment to monetizing stolen data through credential theft.
This latest development underscores the persistent and evolving threat landscape where cybercriminal syndicates continuously refine their malware to bypass modern defenses and target valuable user data.
Who Are the Golden Chickens?
Golden Chickens is a financially motivated threat actor group with roots dating back to at least 2018. The group is best known for the More_eggs malware family, which has been widely used in targeted phishing campaigns. Their operations are typically conducted under the malware-as-a-service (MaaS) model, enabling other threat actors to rent their malicious tools.
Golden Chickens is believed to be associated with the online persona badbullzvenom, reportedly operated by individuals from Canada and Romania. Their previous arsenal includes:
- More_eggs Lite
- VenomLNK
- TerraLoader
- TerraCrypt
- RevC2 (Backdoor)
- Venom Loader
TerraStealerV2: Targeting Browser and Crypto Wallet Data
The newly identified TerraStealerV2 is a data-harvesting malware variant focused on collecting:
- Saved login credentials from web browsers
- Cryptocurrency wallet information
- Browser extension data
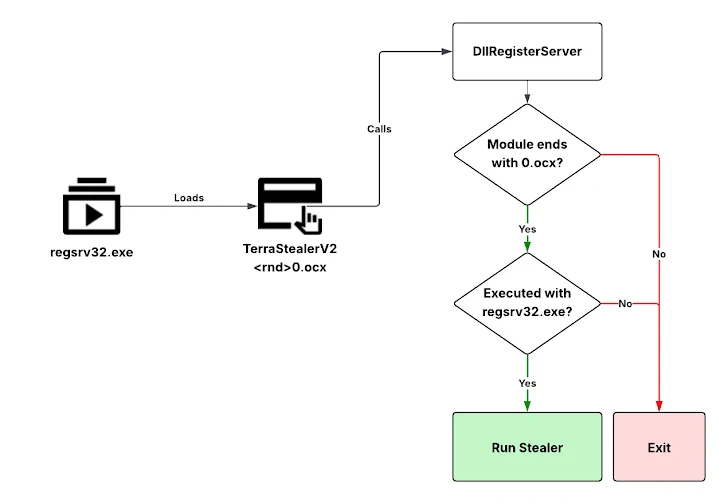
The malware is being distributed through multiple formats:
- .EXE (executables)
- .DLL (dynamic-link libraries)
- .MSI (Microsoft Software Installer packages)
- .LNK (shortcut files)
In each case, the malicious payload is encapsulated as an OCX file (OLE Control Extension) and fetched from an external domain: wetransfers[.]io.
Notable Characteristics
- Targeted Chrome Database: TerraStealerV2 specifically targets Chrome’s
Login Datadatabase. - Encryption Limitation: It fails to bypass Chrome’s Application Bound Encryption (ABE), implemented after July 2024—indicating the malware may be either outdated or still in active development.
- Dual Exfiltration Channels: Exfiltrates data to both Telegram channels and
wetransfers[.]io. - Defense Evasion: Utilizes native Windows utilities like
regsvr32.exeandmshta.exeto avoid detection.
TerraLogger: A New Keylogging Tool
Unlike TerraStealerV2, TerraLogger is a dedicated keylogger that records user keystrokes using low-level keyboard hooks.
Key Characteristics:
- No C2 Communication: Currently does not support exfiltration or command-and-control (C2) communication.
- Data Storage: Keystrokes are written to local files.
- OCX-Based Delivery: Also delivered as an OCX file.
- Intended Use: Likely used alongside other components of the Golden Chickens ecosystem or in standalone mode for less sophisticated attacks.
These features suggest that TerraLogger is either in its early development stages or is meant to be deployed in combination with other malware tools for more comprehensive campaigns.
Broader Malware Landscape: StealC, Hannibal, Nullpoint & More
Golden Chickens’ resurgence with new malware tools comes as part of a broader surge in credential-stealing malware across the threat landscape. Other recently discovered families include:
- Hannibal Stealer
- Gremlin Stealer
- Nullpoint Stealer
Additionally, a new version of StealC malware (v2.2.4) has been observed. It includes:
- Improved C2 protocols with RC4 encryption
- Integrated builder for payload customization based on geolocation, HWID, and installed software
- Support for MSI & PowerShell delivery
- Telegram bot integration for exfiltration alerts
- File grabber & brute-force credential modules
These advancements highlight a growing emphasis on modularity, customizability, and ease of use among malware authors.
Why This Matters
Credential theft remains one of the most lucrative entry points for cybercriminals. With more users relying on browser-stored passwords and software-based crypto wallets, attackers are now optimizing their malware to directly tap into those reservoirs of sensitive information.
Golden Chickens’ return with refined malware tools like TerraStealerV2 and TerraLogger is a stark reminder for organizations and individuals to:
- Implement multi-factor authentication (MFA)
- Avoid storing credentials in browsers
- Use hardware wallets for crypto storage
- Maintain updated anti-malware and endpoint detection systems
- Monitor unusual use of Windows scripting utilities
Final Thoughts
Golden Chickens may be far from extinct. Their latest tools, TerraStealerV2 and TerraLogger, demonstrate that financially motivated threat actors continue to refine their tradecraft, adapting to modern browser security and user behavior.
As malware-as-a-service platforms grow more accessible, it’s crucial for businesses, security teams, and everyday users to stay vigilant. The threat landscape is evolving rapidly—and so should our defenses.
Stay Ahead of Cyber Threats
Subscribe to the SoloSecurities newsletter for weekly updates on the latest in cybercrime, malware trends, and real-time threat intelligence.















Add comment