1. Introduction: A New Russian Cyber Threat
In an era where cyber warfare is becoming as critical as traditional warfare, nation-state hackers are leveraging sophisticated techniques to infiltrate organizations worldwide. One of the latest and most concerning threats comes from Water Gamayun—a Russian-linked cybercriminal group also known as EncryptHub and LARVA-208.
Their latest campaign exploits a newly patched vulnerability in Microsoft Windows (CVE-2025-26633) to deploy two custom backdoors: SilentPrism and DarkWisp. These malware variants are designed for long-term persistence, stealthy data exfiltration, and advanced cyber espionage.
By using MSC EvilTwin, a novel attack technique targeting the Microsoft Management Console (MMC) framework, Water Gamayun has silently infiltrated numerous networks, bypassing traditional security measures.
This attack represents a new level of cyber sophistication, where signed software, trusted system processes, and deceptive infection techniques are combined for maximum impact.
2. The CVE-2025-26633 Vulnerability: A Gateway for Cyber Espionage
Understanding CVE-2025-26633
CVE-2025-26633 is a critical vulnerability in Microsoft’s MMC framework, allowing attackers to execute arbitrary code via maliciously crafted .msc files.
- Impact: Allows remote code execution (RCE) without user interaction.
- Exploitation Method: Rogue Microsoft Console (.msc) files disguised as legitimate system tools.
- Severity Score: 9.8/10 (Critical)
- Affected Systems: All Windows versions with MMC enabled.
Why This Exploit Is Dangerous
This vulnerability is particularly severe because:
✅ Stealthy Execution: .msc files appear as legitimate administrative tools.
✅ Persistent Access: Allows attackers to maintain long-term control over infected systems.
✅ Bypasses Security Solutions: Antivirus and EDR solutions often fail to detect signed .msi files.
✅ Used for Advanced Espionage: Water Gamayun specifically targets government institutions, enterprises, and critical infrastructure.
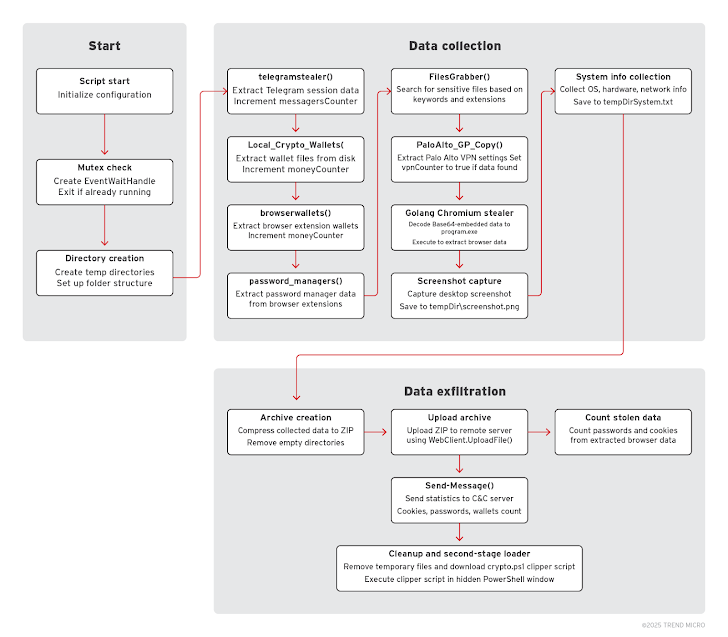
3. Water Gamayun’s Attack Chain: How the Exploit Works
The attack follows a highly sophisticated infection sequence, ensuring stealth, persistence, and data exfiltration.
Step 1: Initial Compromise
The infection begins with phishing campaigns and malicious software downloads, where attackers deploy:
- Provisioning Packages (.ppkg)—Bundles that install malware silently.
- Signed MSI Files—Masquerading as legitimate apps like DingTalk, QQTalk, and VooV Meeting.
- Microsoft Console (.msc) Files—Exploiting CVE-2025-26633 to gain system access.
Step 2: Deployment of SilentPrism and DarkWisp
Once the system is compromised, two backdoors are dropped:
SilentPrism: The Multi-Purpose Backdoor
🔹 Sets Up Persistence – Ensures malware survives reboots.
🔹 Executes Multiple Shell Commands Simultaneously – Allows advanced remote control.
🔹 Anti-Forensic Features – Cleans up traces to evade security analysts.
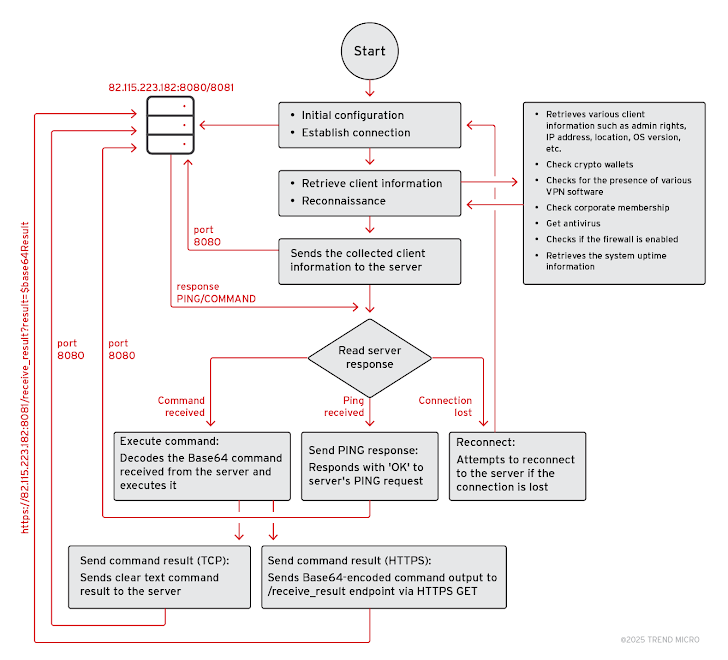
DarkWisp: The Cyber Espionage Toolkit
🔹 Collects System Information – Performs reconnaissance on the infected host.
🔹 Exfiltrates Data – Extracts passwords, Wi-Fi credentials, and sensitive files.
🔹 Stealthy Communication – Uses encrypted TCP connections on port 8080.
Step 3: Command & Control (C&C) Operations
Both malware variants connect to Water Gamayun’s C&C infrastructure, enabling:
✅ Real-time execution of attacker commands.
✅ Downloading additional payloads.
✅ Extracting sensitive data.
4. Advanced Tactics: Why This Attack Is Highly Effective
Living-Off-The-Land Binaries (LOLBins)
Water Gamayun abuses trusted Windows processes to execute malware undetected.
🚨 Example: IntelliJ runnerw.exe is exploited to execute remote PowerShell scripts stealthily.
Multi-Stage Attack Model
Instead of relying on a single infection vector, the attackers deploy:
- EncryptHub Stealer Variants (A, B, C)—Custom malware stealing credentials & system data.
- Commodity Malware (Rhadamanthys, StealC, Amadey, Lumma Stealer, Clippers)—Extracts financial and cryptocurrency data.
Masquerading as Legitimate Software
🚨 Attackers disguise malware as Microsoft-signed MSI installers, allowing them to evade detection.
5. Cyber Espionage & The Bigger Picture
Water Gamayun’s campaign is not just cybercrime—it’s cyber warfare.
- Targets: Governments, multinational corporations, and critical infrastructure sectors.
- Objectives: Long-term data theft, cyber sabotage, and intelligence gathering.
- Implications: Potential disruptions to national security, financial markets, and supply chains.
This attack highlights the growing intersection between cybercrime and geopolitical conflicts, where state-sponsored hackers play a crucial role in modern warfare.
6. How to Defend Against This Threat
1. Patch Management & System Hardening
🔹 Apply Microsoft’s security patches for CVE-2025-26633 immediately.
🔹 Restrict execution of .msc files in high-security environments.
2. Behavioral Analysis & Threat Detection
🔹 Monitor PowerShell execution for suspicious scripts.
🔹 Use EDR solutions to detect anomalous MSI installer activities.
3. Network Monitoring & Anomaly Detection
🔹 Track outbound traffic to detect suspicious TCP 8080 connections.
🔹 Implement network segmentation to limit malware spread.
4. Zero Trust Security Models
🔹 Enforce least privilege access to minimize attack surface.
🔹 Deploy multi-factor authentication (MFA) across critical systems.
7. The Future of Cyber Warfare: What Comes Next?
Water Gamayun’s attack is a glimpse into the future of cyber threats. We can expect:
🔮 More zero-day exploits targeting trusted system components.
🔮 Wider use of AI-powered malware for automated attacks.
🔮 Increase in cyber-espionage against governments & corporations.
Cybersecurity professionals must stay ahead by investing in threat intelligence, AI-driven security tools, and advanced mitigation strategies.
8. Final Thoughts
Water Gamayun’s use of CVE-2025-26633, MSC EvilTwin, SilentPrism, and DarkWisp demonstrates a new level of cyber sophistication. This is not just another malware attack—it’s an evolution in cyber warfare.
👨💻 Action is needed NOW—patch systems, train employees, and strengthen defenses. The cyber battlefield is shifting, and only the prepared will survive.
🔐 Stay Secure. Stay Vigilant.















Add comment